Reach Out For Access
Interested in BYOC? Access is limited to Enterprise customers. Please reach out to our team to get access: privacy@freeplay.aiBYOC at a glance
Bring-Your-Own-Cloud lets you run all Freeplay services inside your own AWS, GCP, or Azure account. You keep full control over data, IAM roles, and network boundaries while Freeplay still updates and supports the software.
Why choose BYOC?
- All prompts and responses remain inside your cloud; Freeplay never receives or stores them. – Meets strict data-residency or internal-only policies.
- Reduced vendor-risk reviews – Auditors see a familiar cloud footprint that you govern.
- Same product feature velocity – Freeplay’s automated control plane delivers signed updates to the Freeplay application.
- Minimal DevOps overhead – when compared to alternative models for privately hosted software, like installing & updating Docker images and setting up & maintaining all of your own serving and database infrastructure
Architecture Overview
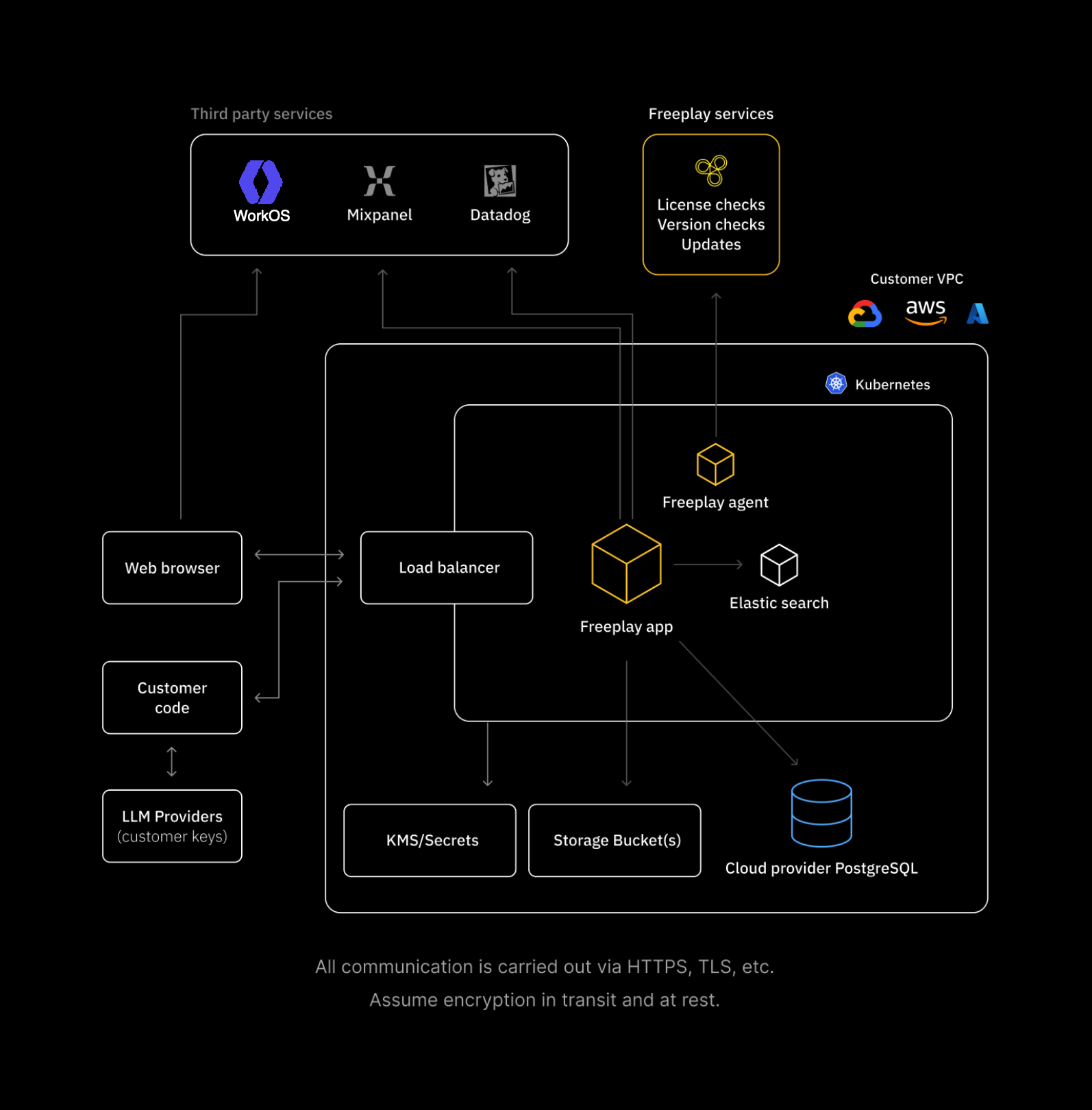
BYOC Deep Dive
How BYOC works
- Prepare your environment - create an empty cloud project or sub-account.
- Deploy the Freeplay agent – Freeplay generates a bundle for you with the installer script. It will guide you through the type of deployment you want (Publicly accessible domain or Private only).
- Provision cluster – Freeplay uses Terraform to provision managed SQL (PostgreSQL), Bucket Storage, and Kubernetes. The Freeplay agent uses Helm to spin up Elasticsearch, NATS, and the Freeplay web application.
- Stay current – the agent polls Freeplay’s control plane for releases and applies rolling upgrades. This is set to poll every 4 hours by default. We suggest turning on ‘automatic updates’ to ensure you receive the latest security fixes and features.
# Example quick-start (AWS)
./freeplay_up.sh
Prerequisites
Presently we provide terraform that provisions everything but the account/project/subscription. Some tweaks may apply depending on the networking architecture by your team. Knowing your network configuration can help expedite the process.
| Item | Requirement |
|---|
| Cloud project | Empty AWS account / GCP project / Azure subscription |
| Kubernetes | 1.27+ (EKS, GKE, AKS) |
| Database | RDS / Cloud SQL: db.t3.medium (2 vCPU, 4 GB) or larger |
| Object storage | S3 / GCS / Blob Storage bucket (any class) |
| IAM | Temporary admin role for the installer → least-privilege roles generated afterward |
| Networking | Public or private subnets with NAT; optional VPC peering or Private Link |
| Outbound egress | Replicated, WorkOS, Datadog, Mixpanel (HTTPS only, see domains below) |
AWS Services and IAM
AWS does not require enabling services like GCP or registering providers like Azure — services are available by default in your account. The deployment primarily requires appropriate IAM permissions.
# AWS Services Used
## Compute & Containers
EKS (Elastic Kubernetes Service)
EC2 (for NAT Gateway, bastion VM)
## Database
RDS (PostgreSQL)
## Storage
S3 (for assets and data export)
## Security & Secrets
Secrets Manager
KMS (Key Management Service)
IAM (Identity and Access Management)
## Networking
VPC, Subnets, Security Groups
NAT Gateway
Elastic Load Balancing
## DNS & Certificates
Route53
ACM (Certificate Manager)
## Monitoring
CloudWatch Logs
# IAM Permissions
## For the deployment user/role (admin-level or scoped)
eks:*
ec2:*
rds:*
s3:*
secretsmanager:*
kms:*
iam:* (for creating IRSA roles)
route53:*
acm:*
elasticloadbalancing:*
logs:*
## For EKS workload identity (IRSA)
s3:PutObject, s3:GetObject, s3:ListBucket (on Freeplay buckets)
secretsmanager:GetSecretValue, secretsmanager:DescribeSecret (on DB secrets)
kms:Decrypt, kms:DescribeKey (on encryption key)
route53:ChangeResourceRecordSets, route53:List* (for external-dns)
## For Bedrock access (optional)
bedrock:InvokeModel, bedrock:InvokeModelWithResponseStream
sts:AssumeRole (to assume Bedrock role)
Google Cloud APIs and IAM
These APIs will be necessary for the deployment on Google Cloud. We use least-privileged permissions where possible. We suggest keeping things isolated by project. The ./freeplay_up.sh script will request these APIs prior to installing the terraform.
# APIs that should be on
## Needed for GKE
compute.googleapis.com
container.googleapis.com
## Needed so GKE workload identity can access other Google services
iam.googleapis.com
## Needed for provisioning DB, adding users that the app uses
sqladmin.googleapis.com
## Needed for secure secrets and encryption of data into Postgres/Buckets
secretmanager.googleapis.com
cloudkms.googleapis.com
## Needed for ability to provision certificate so site is securely accessible
dns.googleapis.com
certificatemanager.googleapis.com
servicenetworking.googleapis.com
## Needed to store events and multimedia assets securely
storage.googleapis.com
## Needed for access to Vertex
aiplatform.googleapis.com
## These may be necessary for any VPC peering scenarios
networksecurity.googleapis.com
networkmanagement.googleapis.com
privateca.googleapis.com
# IAM Roles
## For asset and data buckets that are provisioned in deployment (nothing else)
roles/storage.objectAdmin
## For cluster service account can access Google Managed Services
roles/iam.workloadIdentityUser
roles/cloudsql.client
roles/secretmanager.secretAccessor
roles/cloudkms.cryptoKeyEncrypterDecrypter
## For cluster nodes to provide metrics
roles/logging.logWriter
roles/monitoring.metricWriter
roles/monitoring.viewer
roles/stackdriver.resourceMetadata.writer
roles/storage.objectViewe
## For the designated cluster admin (optional)
roles/container.admin
Azure Resource Providers and Roles
These resource providers must be registered in your Azure subscription. The ./freeplay_up.sh script will check for these prior to running Terraform.
# Resource Providers that must be registered
## Needed for AKS
Microsoft.ContainerService
## Needed for VNet, subnets, NSG, NAT Gateway, Private DNS, and peering
Microsoft.Network
## Needed for secure secrets and encryption keys
Microsoft.KeyVault
## Needed to store events and multimedia assets
Microsoft.Storage
## Needed for PostgreSQL Flexible Server
Microsoft.DBforPostgreSQL
## Needed for workload identity and managed identities
Microsoft.ManagedIdentity
## Needed for Log Analytics workspace
Microsoft.OperationalInsights
## Needed for bastion VM (optional)
Microsoft.Compute
# Azure Roles
## For the deployment service principal or user
Contributor (on resource group)
User Access Administrator (on resource group)
## For the AKS workload identity
Storage Blob Data Contributor (on storage accounts)
Key Vault Secrets User (on Key Vault)
DNS Zone Contributor (on DNS zone)
## For AKS cluster admins
Azure Kubernetes Service RBAC Cluster Admin (on AKS cluster)
Security & compliance
- Data residency – all sensitive customer data including prompts, responses, and evaluations stay in your cloud account. Optional ability to share support bundles for troubleshooting scenarios.
- Secrets – stored in your cloud KMS‐backed secret manager; never transmitted to Freeplay.
- Updates – releases are signed and verified before install; only metadata (version, health ping) is sent to the control plane.
Costs
- Freeplay subscription – BYOC is available only for Enterprise-tier contracts. Please contact Sales for more info about access.
- Your cloud – you pay for all nodes, database, Elasticsearch, storage, and egress. Typical mid-sized install runs ≈1.2k−2k/mo in AWS us-east-1.
BYOC Outbound Egress Requirements
All outbound traffic uses port 443 / HTTPS (TLS 1.2+).
1. Replicated (Required)
| |
|---|
| Domains | *.replicated.com, *.replicated.app |
| Purpose | Agent polls for signed application & infrastructure releases |
| Data transmitted | Agent ID, current version, signed artifacts |
| IP ranges | replicatedhq/ips |
| Firewall rules | Replicated Customer Firewalls |
2. WorkOS Authentication (Required)
| |
|---|
| Domains | *.authkit.app, *.workos.com |
| Purpose | User authentication and authorization |
| Data transmitted | User email |
| IP ranges | Cloudflare published ranges — see WorkOS On-Prem Deployment and Cloudflare IPs |
3. Datadog (Conditional)
| |
|---|
| Domains | *.datadoghq.com (regional endpoints) |
| Purpose | Metrics and traces for 24×7 ops SLA |
| Data transmitted | Health metrics, cluster stats, anonymous performance metrics, scrubbed logs (no prompt/response content) |
| IP ranges | ip-ranges.datadoghq.com |
4. LLM Provider Endpoints (Conditional)
| |
|---|
| Domains | Provider-specific (e.g., api.openai.com, bedrock-runtime.*, *.anthropic.com, Azure OpenAI endpoints) |
| Purpose | Inference calls initiated by Freeplay application |
| Data transmitted | Prompts, context, parameters, model responses |
| Required? | Yes, if you use external hosted models |
| How to restrict | Use VPC endpoints or Private Link where the provider offers them |
5. Mixpanel (Optional)
| |
|---|
| Domains | *.mixpanel.com |
| Purpose | Product-usage analytics (UX insights) |
| Data transmitted | Anonymous instance ID, UI events (no sensitive prompt/response data) |
| How to disable | Set the Mixpanel token to empty via the KOTS admin panel |
Destinations 1, and 2 are always required for a supported install. 3 is strongly recommended. Destination 4 is required only when your workloads invoke external hosted models — BYOC also supports running local/on-site models if you need zero data egress for LLM traffic.
- You decide which LLM providers and regions to enable in the Freeplay UI.
- All calls use HTTPS (TLS 1.2+).
- Freeplay’s log policy prevents user content from landing in Datadog.
- If you need a completely offline install, talk to us. An artifact-mirror and on-prem observability stack are on the roadmap.
FAQ
| Question | Answer |
|---|
| Can we air-gap entirely? | Not yet. The agent needs periodic egress for updates and license checks. |
| Is bring-your-own-KMS-store supported? | Yes. We store all encryption keys on a KMS in your account. |
| What about bring-your-own VPC or cluster? | Yes. While a vanilla cluster may be easier, you may have pre-established rules that work for your vpc or cluster. |
| Can I scale horizontally? | The Helm values file exposes replicas and resources; autoscale works like any K8s app. |
| Private-only access? | Yes. The installer script will ask if you want to peer to an existing VPC. You’ll be responsible for further peering. |
| Is the site reachable from the public Internet? | We can provision either a public internet site, or create a private site that is only resolvable or firewalled to your virtual network or connection. |
| What persistent storage is part of this deployment? | • Managed Cloud SQL / RDS / Azure SQL Database (PostgreSQL) • S3 / GCS / Blob storage for multi-modal artifacts • Block storage (EBS / PD / Disk) for Elasticsearch indices and NATS |
| I’ve heard Kubernetes can be unreliable with persistent volumes. Does that put my data at risk? | No. BYOC keeps the source-of-truth in a managed database service such as Amazon RDS, Cloud SQL, or Azure PostgreSQL that runs outside Kubernetes. Everything stored on in-cluster volumes (search indices, NATS JetStream, temporary files) can be rebuilt from that database. If a node or the whole cluster is lost, you simply spin up new nodes, redeploy the chart, and point it at the same database. The application comes back with no data loss. |
| Can I connect BYOC to my existing Kubernetes cluster, Elasticsearch stack, or shared database? | Not today. BYOC runs in an isolated project or account so Freeplay can manage scaling, upgrades, and support without impacting your other workloads. This isolation also lets us guarantee performance, security boundaries, and fast root-cause analysis. |
| Is there a terraform backend? | It is hosted on an s3 (or equivalent bucket) in your cloud. This means the state can be preserved with a storage backend within your perimeter |
| Can I preview the terraform and networking rules/IAM policies/etc? | Yes, please contact us. |


